TEMPEST workshop presentation, Riga, october 2008
Table of Contents
TEMPEST
TEMPEST - encoding that which is.

Any time a machine is used to process classified information electrically, the various switches, contacts, relays, and other components in that machine may emit radio frequency or acoustic energy.
… This problem of compromising radiation we have given the covername TEMPEST.
[TEMPEST: A Signal Problem. NSA 1972]
-
A one day practical and theoretical workshop exploring contemporary paranoia/ontology as a tale of so-called compromising emanations (CE).
TEMPEST… presents a practical introduction to the modulation and demodulation of any signal, allowing a fresh perspective on the digital as primary material; the transition into a digital realm which humbles its carrier, submitting the aether to the status of a lowly medium; that which is modulated.
TEMPEST… underscores a rich adventure, making sense of fortuitous emanations of sound, light and, primarily, electromagnetic phenomena using simple apparatus and theory. Research topics for artistic examination include, but are not limited to: signals and noise, van Eck phreaking, decoding, encryption and hiding, surveillance, information and carrier/support, intentionality of CE.
Finally, TEMPEST, as covername; the word itself as revealing a certain relation to both hiding (information) and the state (subject). TEMPEST, as term, supposedly means nothing, quite simply denying the possibility of being decoded as itself an acronym. A codeword for the exposure of the world as (being) encoded.
What exactly is TEMPEST?
- 1] TEMPEST as codename

refers to the study and potential control of compromising emanations (CE) which can be used to recover the plain text (or other information) of encoded/national security related nature. CE potentials include acoustic, and electromagnetic radiation [including in this wide spectrum visible light (optical emanations)]
Compromising emanations are [ thus] defined as unintentional intelligence-bearing signals which, if intercepted and analyzed, may disclose the information transmitted, received, handled, or otherwise processed by any information-processing equipment.
[Wikipedia - note the relation to intentionality and intelligence]
TEMPEST is a form of side-channel attack [In cryptography, a side channel attack is any attack based on information gained from the physical implementation of a cryptosystem, rather than brute force or theoretical weaknesses in the algorithms … For example, timing information, power consumption, electromagnetic leaks or even sound can provide an extra source of information which can be exploited to break the system.[Wikipedia]]
EMSEC (Emissions Security) as contemporary term. Also note use of RED and BLACK sectors:
"A RED equipment or circuit is one that handles plain text information with national security value. Equipment processing signals that are unclassified, either because of content of the text or because the intelligence is obscured by encryption, is denoted in BLACK."
Exploit examples:
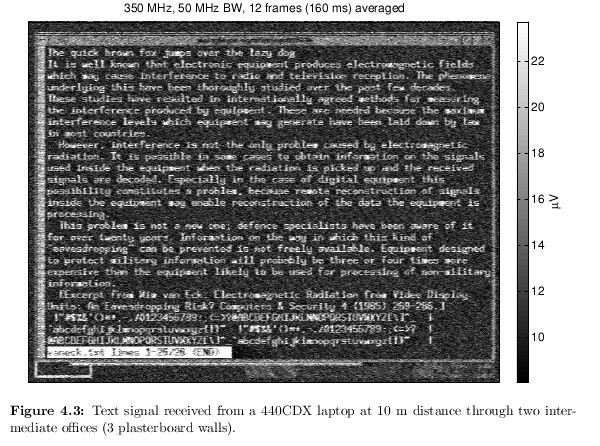
Remote reconstruction of a computer monitor screen/desktop by way of received EM emissions from the video card, cables and CRT/laptop screen.
Unintentional radiation of useful information from the local oscillators of some receivers.
Reconstruction of data leaked from a serial line through wires and Ground acting as an antenna.
Access to information from a monitor or screen by way of leaked or reflected light emissions.
other terms of interest: TEAPOT, HIJACK, NONSTOP
- TEAPOT:
Intentional hidden use of a TEMPEST line of transmission (for example by Trojan software to transmit sensitive data without detection). AKA soft TEMPEST.
- HIJACK and NONSTOP:
NONSTOP is a classified codeword that apparently relates to a form of compromising emanations, but involves the transmittal of the signals from radio frequency devices (handheld radio, cell phone, pager, alarm system, cordless phone, wireless network - AM/FM commercial broadcast receivers are excluded) in proximity to a device containing secure information. There are specific guidelines for either turning the RF device off, or keeping it a certain distance away from the secure device (PC, printer, etc.).
HIJACK appears to relate to similar phenomena of cross-modulation.
2] TEMPEST as a revealing (of (making) light)

of that which is hidden (revelation)
as a reverse engineering of the world become information
3] TEMPEST documentation
as paralleling the texts of alchemy - obscuring details of implementation, intentional mistakes to trip up the uninitiated
an intentional recursion of codenames
4] TEMPEST as a reflective model…

for "perception", as a reflexive model for consciousness/rationalism
- each stage of the model examined: -detection -decoding -reconstruction
- making of a model
5] TEMPEST as being revealed
(the already signalled or encoded). Model revelation (pink light).
6] TEMPEST as control through:
7] TEMPEST as a crossing or exchange
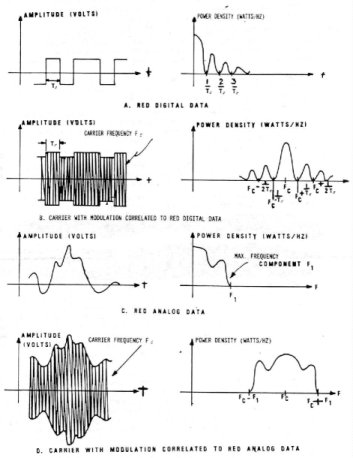
of wavelengths and domains
- all is information and potential intelligence signal
[paranoia]
TEMPEST philosophy
// from spectropia notes/text
In this masqueraded history of doubles, the always already coded phenomena of TEMPEST provides an easy entry for (theories of) paranoia, and conspiracy - an essential existential relation to the matter which provides a decent lens to observe a parallel (contemporary) landscape of modulation and demodulation, all manner of coherence and detection borrowed from technical terms within the radio day.
On one side of a signal/noise mirror glass, being the ones always to be compromised, and foreshadowing our rather fishy closing message, TEMPEST is precisely a codename referring to the "investigation and study of compromising emanations" with the latter terms defined as "Unintentional data-related or intelligence-bearing signals that, if intercepted and analyzed, could disclose the information being transmitted, received, handled, or otherwise processed by any information processing equipment" according to the NASA Automated Information Security Handbook 1. TEMPEST refers also to the control of such compromising (aetheric or ectoplasmic even) emanations, within the heady recursion of its own undecodable acronym, with these facts concerning the title suggesting an ideal military state of secrecy, of containment. TEMPEST is thus exactly a codename for that which is always coded in advance - the message after Gnosticism.
_
TEMPEST, as a paranoiac form of making sense, becomes part of the inverted message-time, that which is always yet to be sent in arriving now, purely as a literary phenomena, some kind of genre confusion between detective fiction and aplay with the logic of sense and language which results in the coded detection novel exemplified by William S. Burrough's Cities of the Red Night
Both this literature, and a return to Eddington, again by way of the opening quotation, is made clear here:
Our account of the external world (when purged of the inventions of the story teller in consciousness) must necessarily be a "Jabberwocky" of unknowable actors executing unknowable actions … We must seek a knowledge which is neither of actors nor of actions, but of which the actors and actions are a vehicle. The knowledge we can acquire is knowledge of a structure or pattern contained in the actions.
[Sir Arthur Stanley Eddington. New Pathways in Science 2007. pp. 256]
TEMPEST history
see also: TEMPEST timeline: http://cryptome.org/tempest-time.htm
early history on the wire

telegraphy, telephony and crosstalk (also assistant of Edison)
I used to spend hours at night in the laboratory listening to the many strange noises in the telephone and speculating as to their cause. One of the most common sounds was a snap, followed by a grating sound that lasted two or three seconds before it faded into silence, and another was like the chirping of a bird. My theory at this time was that the currents causing these sounds came from explosions on the sun or that they were signals from another planet. They were mystic enough to suggest the latter explanation but I never detected any regularity in them that might indicate they were intelligent signals.
[Thomas A. Watson, Exploring Life: The Autobiography of Thomas A. Watson]
link to EVP and "natural radio"
the invention of frequency, of an intentional signal (intendent modulation schemes and carriers)
1914
The first appearance of compromising emanations in warfare seems to date to 1914. Field telephone wires were laid parallel to enemy trenches to connect the troops with their headquarters. The effect was again cross-talks. Listening posts were quickly established and protective measures were introduced, including the use of twisted-pair cable.
Mid-1950s
The exact date is not known in public, but it happens sometime in 1950, when the U.S. Government becomes concerned about the Emission Security problem and establishes the TEMPEST Program. The first TEMPEST standards were developed to deal with the increasing danger of espionage.
1950s Berlin tunnel wiretaps:


1960s
In 1960 was the british secret service MI5 ordered to eavesdrop the French embassy in the course of negotiations about joining the European Economic Community. The crypto analysts were not able to decrypt the enciphered signal from the French embassy, but they noticed a faint secondary signal, which was the plain text.
TEMPEST, A Signal problem

(classified document 1972. declassified 2007) relates TEMPEST discovery to 1962
Wim Van Eck 2, van Eck phreaking

Late 1990s:
military exposure
Markus Kuhn - optical emanations
TEMPEST technology
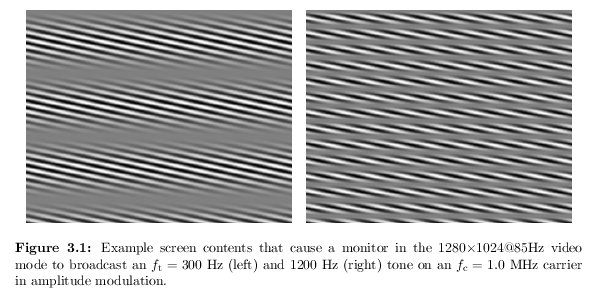
A question of electromagnetism (or of any signal) and the coming into being of frequencies (time domain analysis, Fourier transform - to frequencies, decomposition of a signal)
- EM - basic theory. antenna architecture
detection or collection amplification demodulation analysis/making sense - repetition of data reconstruction of the original
VDU reconstruction/Van Eck phreaking

video theory. synchronisation. simplest apparatus??? [VCR tuner]. horizontal and vertical frequencies
- The vertical diverting signal works in lower kHz band.
- The horizontal diverting signal works in lower MHz band (Long and medium wave).
- The video signal has frequencies up to 100 MHz.
changes in frequency - information content and modulation
pixel clock and other clocks in the computer.
see: xvidtune -show
- acoustic
- optical emanations.
visible light

also printers, serial ports, system buses, LED examples
practical experiments and discussion
schedule -
- Practical demonstrations of TEMPEST-related phenomena and eavesdropping practices
simple demo with radio and monitor
TEMPEST for Eliza

./tempestforeliza 65000000 1024 768 1344 1500000 songs/forelise - 10 MHz
[note using xvidtune -show to uncover the modeline settings such as frequency and full pixel height and width]
Practical collective investigations
exploring emanations of EM presence, and light from constructive perspectives
- EM

sniffing with simple receiver around PC and environment
use of devdisplay software for TEMPEST loopback:
rec -V -t raw -u -1 -c 1 -r 48000 - | devdisplay 200 200 [to add in blocksize]
use of TV for ghosted TEMPEST presences
use of SDR/USRP: peaks, demodulation
usrp_fft.py -R B -g 59 -W -f 640M -d 16
./usrp_tv_rcv.py -R B -f 519.25M -g 59 -d 8 -8
- light
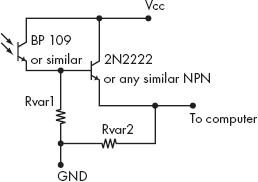
- small router or switch analysis with photodiode and amplifier
Simple C code for phototransistor TEMPEST using BPW42 and parallel port
./temppar <delay>
[NOTE: reboot, check parallel port address and simple settings]
- attempted (re)construction
construction of TEMPEST phenomena
- Final discussion of research and future projects
appendix and references
artists working with TEMPEST:
Erich Berger: http://randomseed.org/tempest/
Gisle Froysland: http://www.bek.no/~gif/tempest/
references:
- optical emanations
Markus G. Kuhn: Optical Time-Domain Eavesdropping Risks of CRT Displays, Proceedings 2002 IEEE Symposium on Security and Privacy, Berkeley, California, 2002:
- acoustic emanations
- general resources
TEMPEST for Eliza: http://www.erikyyy.de/tempest/
Collected TEMPEST resources: http://www.eskimo.com/~joelm/tempest.html
Wim Van Eck's paper: http://jya.com/emr.pdf
TEMPEST timeline: http://cryptome.org/tempest-time.htm
TEMPEST glossary: http://cryptome.org/ncsc-3.htm
http://csrc.nist.gov/publications/secpubs/tempest.txt
Compromising Emanations (Markus G. Kuhn, PDF): http://www.cl.cam.ac.uk/techreports/UCAM-CL-TR-577.pdf
Eckbox: http://eckbox.sourceforge.net/
[decoding screen]
Tinfoil Hat Linux: http://tinfoilhat.shmoo.com/readme.txt
[countermeasures]
Soft Tempest: Hidden Data Transmission Using Electromagnetic Emanations Markus G. Kuhn and Ross J. Anderson (Information Hiding Workshop,1998)
Hidden Data Transmission by Controlling Electromagnetic Emanations of Computers:
http://abaababa.ouvaton.org/tempest/?lang=en
http://bss.sfsu.edu/fischer/IR 360/Readings/tempest.htm
Using VCR tuner: http://cryptome.org/qd-tempest.htm
Sync: http://cypherpunks.venona.com/date/1997/05/msg00123.html
Date: 2009-12-31 15:54:49 GMT
HTML generated by org-mode 6.31trans in emacs 23

